Amazon EKS Workshop > Beginner > Mounting secrets from AWS Secrets Manager > Prepare secret and IAM access controls
Prepare secret and IAM access controls
This workshop has been deprecated and archived. The new Amazon EKS Workshop is now available at www.eksworkshop.com.
Set variables
Verify AWS_REGION variable.
test -n "$AWS_REGION" && echo AWS_REGION is "$AWS_REGION" || echo AWS_REGION is not set
If not set, then complete Start the workshop instructions and verify again.
Set the cluster name variable.
export EKS_CLUSTERNAME="eksworkshop-eksctl"
Create a test secret with the AWS Secrets Manager.
aws --region "$AWS_REGION" secretsmanager \
create-secret --name DBSecret_eksworkshop \
--secret-string '{"username":"foo", "password":"super-sekret"}'
Get secret’s ARN.
SECRET_ARN=$(aws --region "$AWS_REGION" secretsmanager \
describe-secret --secret-id DBSecret_eksworkshop \
--query 'ARN' | sed -e 's/"//g' )
echo $SECRET_ARN
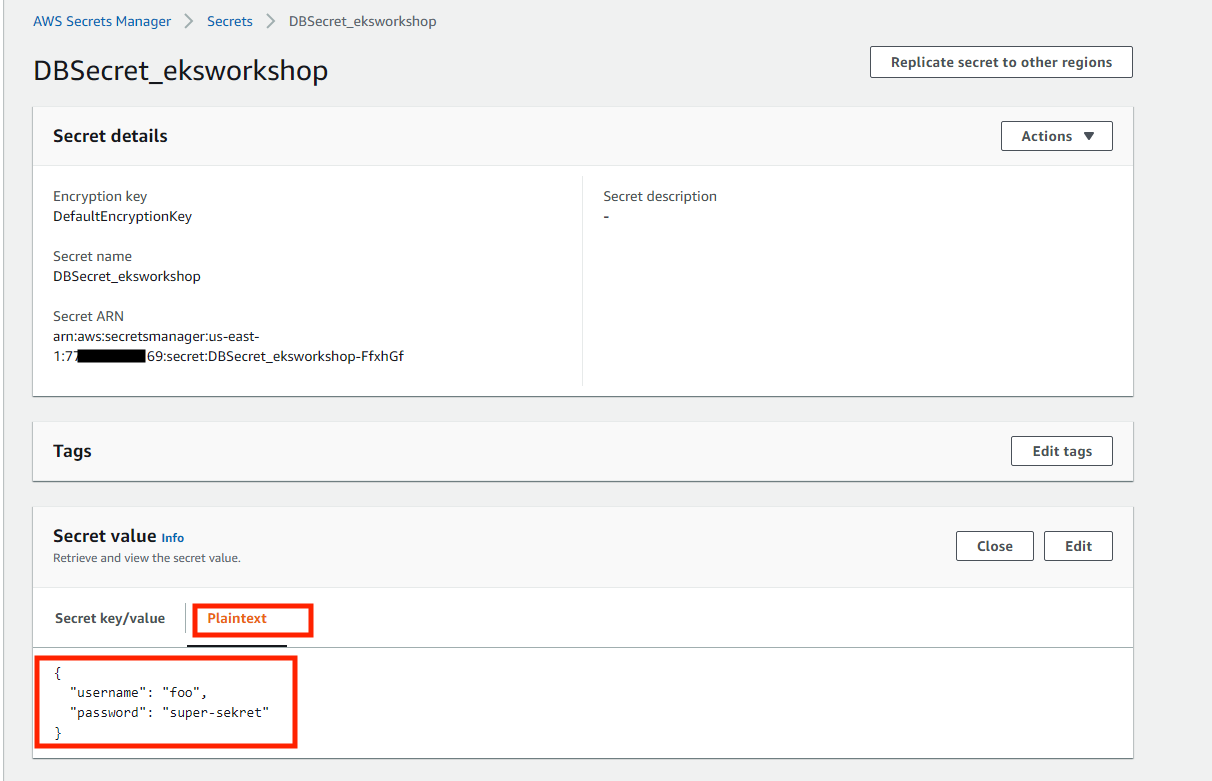
You can also verify the newly created secret via AWS console under AWS Secrets Manager
Create an IAM policy
Create an IAM with permissions to access the secret.
IAM_POLICY_NAME_SECRET="DBSecret_eksworkshop_secrets_policy_$RANDOM"
IAM_POLICY_ARN_SECRET=$(aws --region "$AWS_REGION" iam \
create-policy --query Policy.Arn \
--output text --policy-name $IAM_POLICY_NAME_SECRET \
--policy-document '{
"Version": "2012-10-17",
"Statement": [ {
"Effect": "Allow",
"Action": ["secretsmanager:GetSecretValue", "secretsmanager:DescribeSecret"],
"Resource": ["'"$SECRET_ARN"'" ]
} ]
}')
echo $IAM_POLICY_ARN_SECRET | tee -a 00_iam_policy_arn_dbsecret
Create a Service Account with IAM role
User IRSA and create an IAM role bound to a service account with read access to the secret.
eksctl utils associate-iam-oidc-provider \
--region="$AWS_REGION" --cluster="$EKS_CLUSTERNAME" \
--approve
eksctl create iamserviceaccount \
--region="$AWS_REGION" --name "nginx-deployment-sa" \
--cluster "$EKS_CLUSTERNAME" \
--attach-policy-arn "$IAM_POLICY_ARN_SECRET" --approve \
--override-existing-serviceaccounts